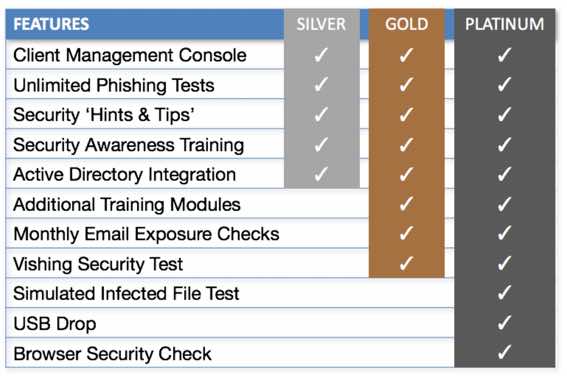
Master Concept partners with KnowBe4, to provide security awareness training to prevent social engineering attacks | Master Concept

CyRAACS™ - Your Trusted Security Partner on Twitter: "Cybercriminals have become experts at social engineering skills, tricking employees into clicking on malicious links that initiate attacks. No security control is perfect —

![Social Engineering Tactics101: 18 ways to hack a human [INFOGRAPHIC] Social Engineering Tactics101: 18 ways to hack a human [INFOGRAPHIC]](https://blog.knowbe4.com/hubfs/smartfile-social-engineering-infographic-100652043-large.idge.png)

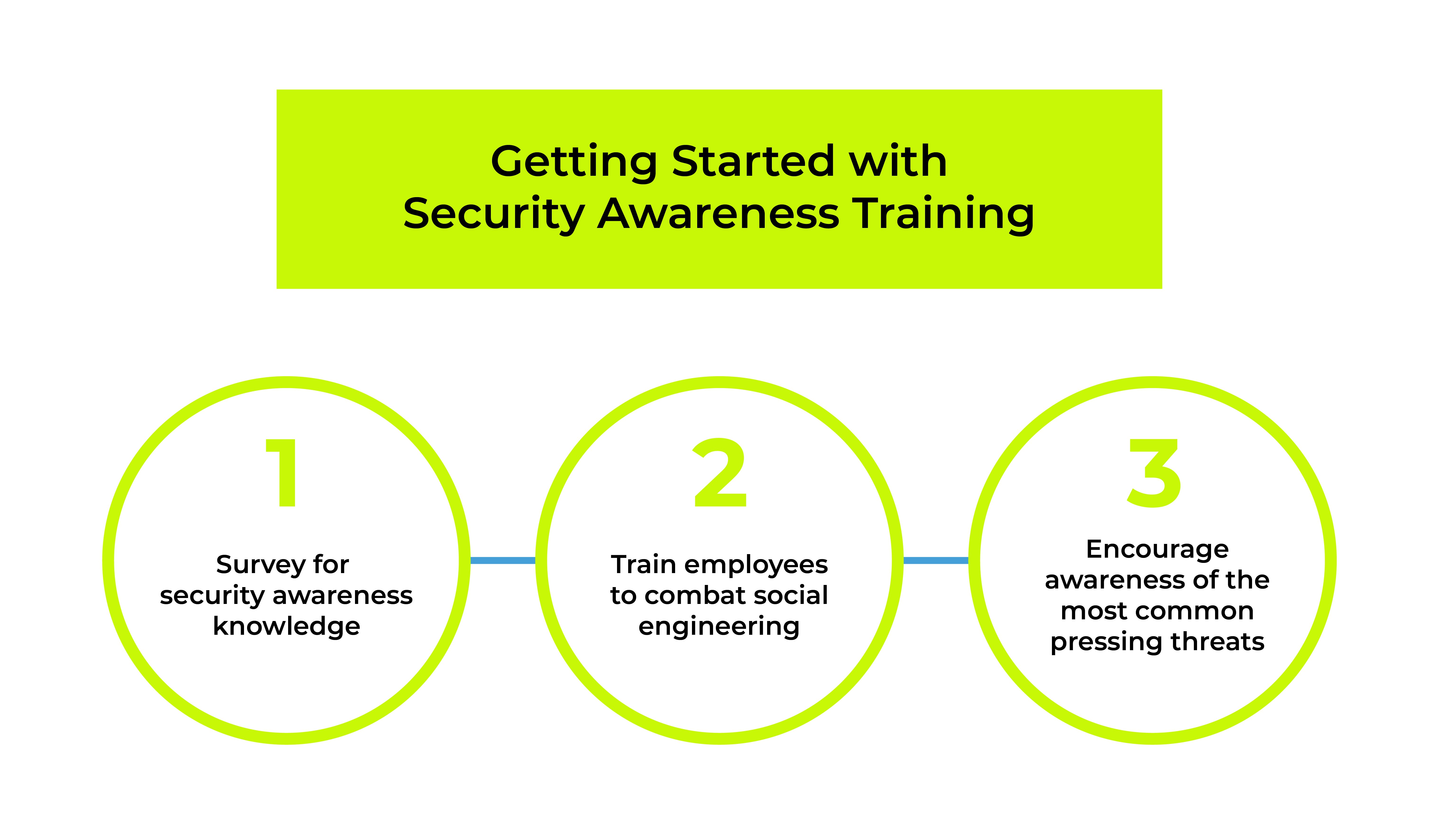


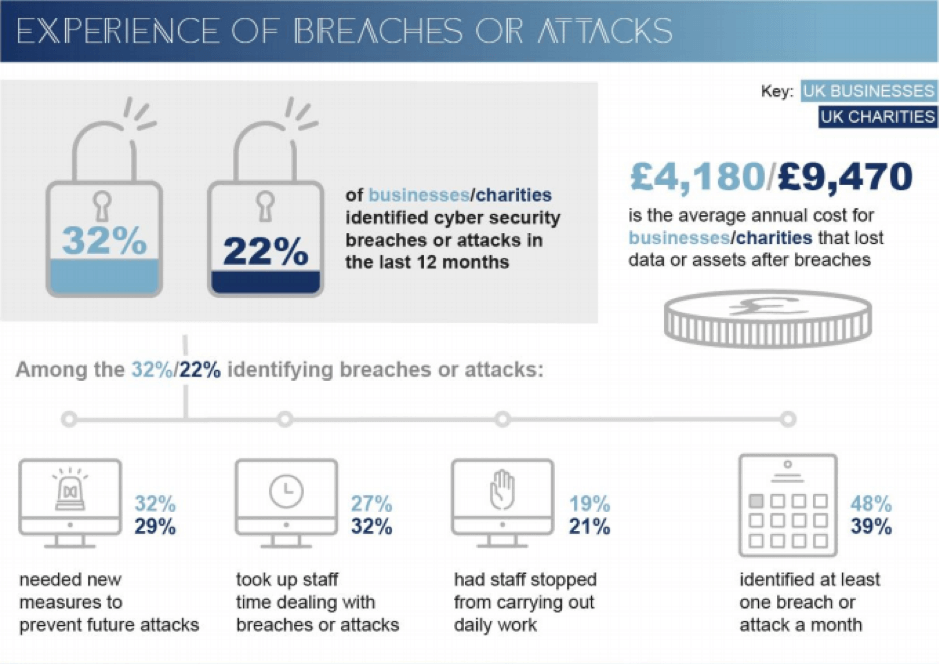




![INFOGRAPHIC] Social Engineering INFOGRAPHIC] Social Engineering](https://blog.knowbe4.com/hubfs/SocialEngineering.jpg)